As more organisations embrace cloud-based and containerized applications, keeping these environments secure becomes crucial. Kubernetes is a powerful tool for managing containers, but it also introduces security challenges. That’s where tools like Trivy and Trivy-Operator can help, enabling teams to detect security risks in their containerized apps and take quick action to keep them secure. In this post, we’ll explain how Trivy and Trivy-Operator work, their key benefits, and how they can be connected to monitoring tools like Grafana and Prometheus for real-time tracking. We’ll also cover how to back up security reports to AWS S3 for long-term storage and compliance.
What is Trivy?
Trivy is an open-source security tool created by Aqua Security that scans container images, file systems, and code for vulnerabilities. It’s known for being quick, easy to use, and highly compatible with different systems. Here’s what makes Trivy a great choice:
- Thorough Vulnerability Scanning: Trivy checks for security issues using databases like the National Vulnerability Database (NVD) and GitHub’s security advisories.
- Quick and Simple Scanning: Trivy’s command-line interface (CLI) makes it easy to scan images, which works well for integrating into CI/CD pipelines.
- Broad Compatibility: Trivy can scan a wide range of operating systems and package managers, so it’s adaptable to different environments.
Example Use Case:
If a team is using Docker for containers, they can add Trivy to their CI/CD pipeline (the process that builds and tests their code) to automatically scan images before deploying them, ensuring that each release is secure.
Introduction to Trivy-Operator
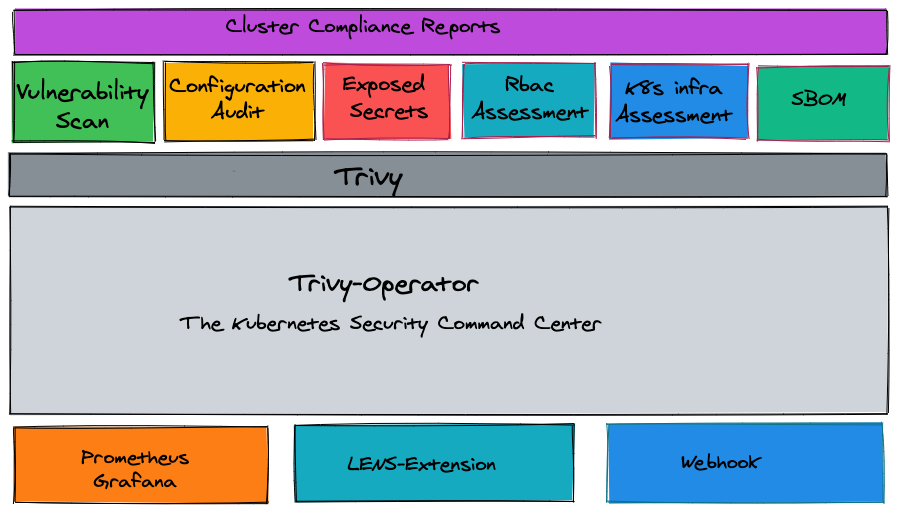
Trivy-Operator is an extension of Trivy that’s tailored for Kubernetes. Unlike Trivy, which is generally run as a separate tool, Trivy-Operator operates directly in a Kubernetes cluster, scanning workloads continuously for vulnerabilities and configuration issues. Key features include:
- Continuous Monitoring: Trivy-Operator scans Kubernetes workloads regularly without disrupting performance.
- Centralised Reporting: By using Kubernetes' own reporting system, Trivy-Operator makes it easy to access security information for all resources in one place.
- Automated Fix Recommendations: Trivy-Operator provides helpful suggestions for fixing issues, making it easier for teams to address vulnerabilities quickly.
Example Use Case:
In a production Kubernetes cluster, Trivy-Operator can be deployed to keep an eye on vulnerabilities in real-time, enabling fast responses to new security issues.
Benefits of Using Trivy and Trivy-Operator Together
Using both Trivy and Trivy-Operator gives you a complete approach to container and Kubernetes security. Here are some of the main advantages:
- Security from Development to Production: Trivy scans container images during development, while Trivy-Operator provides ongoing monitoring in production, ensuring continuous security.
- Continuous Monitoring: Trivy-Operator alerts your team to new vulnerabilities that arise after deployment, reducing security risks.
- Easier Vulnerability Management: Trivy-Operator organises vulnerabilities within Kubernetes, making it easier to keep track of and fix issues.
- Simplified Compliance Reporting: With Trivy-Operator’s detailed reports, your team has the documentation needed for audits, which is especially useful in regulated industries.
How to Set Up Trivy and Trivy-Operator
Here’s a simple guide to getting Trivy and Trivy-Operator up and running in your Kubernetes environment:
Step 1: Install Trivy
- To install Trivy, enter the following command:
brew install aquasecurity/trivy/trivy
Reference: Installation - Trivy
Step 2: Add Trivy to Your CI/CD Pipeline
- Configure Trivy to scan container images in your CI/CD pipeline with a command like this:
trivy image <your-image-name>
Step 3: Deploy Trivy-Operator in Kubernetes
- To install Trivy-Operator, use Helm (a tool for Kubernetes installations):
helm repo add aqua https://aquasecurity.github.io/helm-charts/ helm repo update helm install trivy-operator aqua/trivy-operator --namespace <your-namespace>
Step 4: Review Vulnerability Reports
- Use kubectl to check reports generated by Trivy-Operator:
kubectl get vulnerabilities -n <namespace>
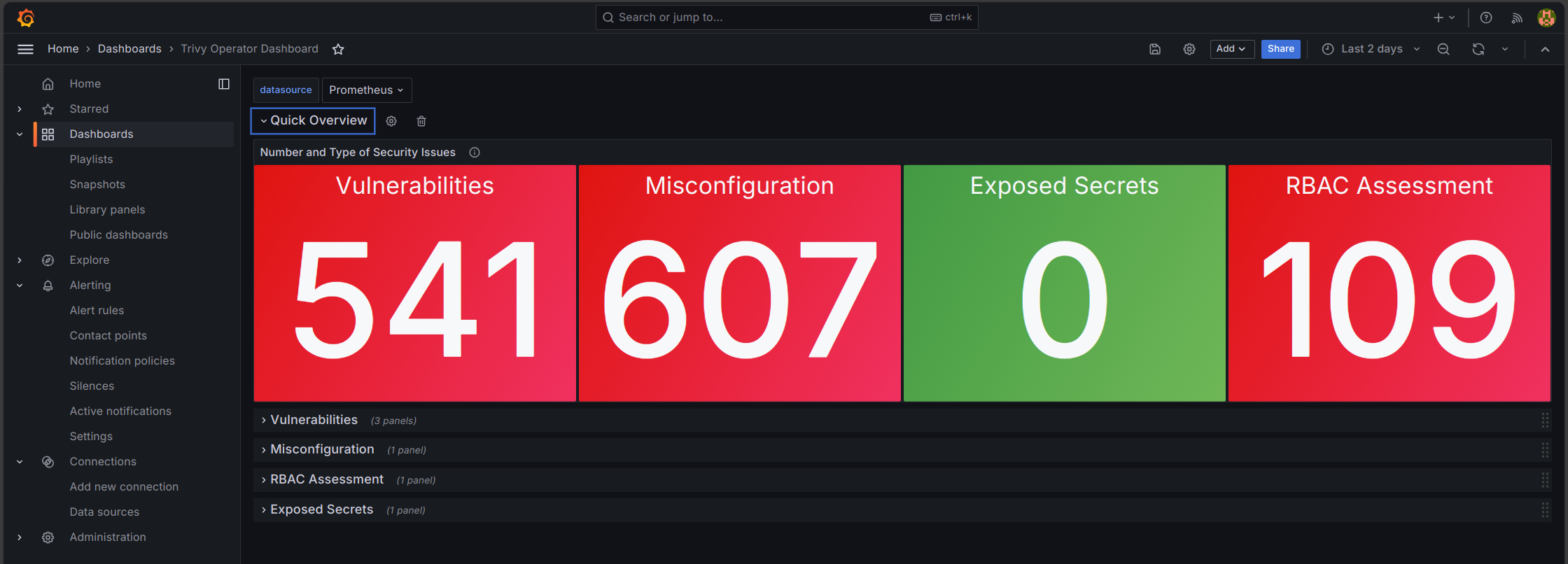
Connecting Trivy-Operator to Grafana and Prometheus
To keep a close watch on your Kubernetes security, you can link Trivy-Operator with monitoring tools like Grafana and Prometheus. This setup enables real-time tracking of vulnerabilities and alerts when needed.
- Prometheus Integration: Trivy-Operator provides security data (e.g., vulnerability counts and severity levels) in a format Prometheus can read. Prometheus then saves this data in a time-series database, making it easy to monitor security trends.
- Grafana Dashboards: With data from Prometheus, Grafana can display customised dashboards to visualise security metrics, such as:
- Vulnerability trends over time
- Severity levels of vulnerabilities
- Impacted workloads or namespaces
- Alerting: Set up alerts in Prometheus or Grafana to notify your team when certain conditions are met, such as when critical vulnerabilities are found. This ensures that your team can respond to security issues quickly.
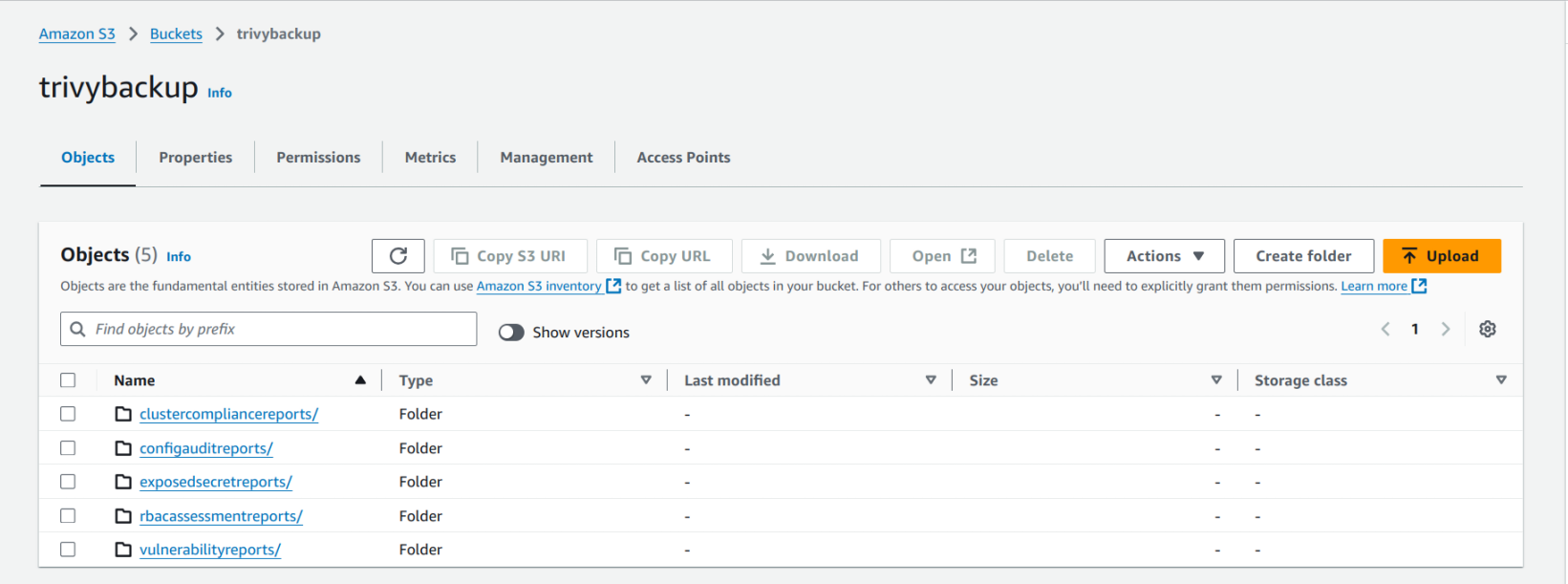
Backing Up Trivy-Operator Reports to S3
To make sure security reports are safely stored for compliance and future reference, you can back up Trivy-Operator’s reports to an AWS S3 bucket.
Step 1: Set Up an S3 Bucket
- In your AWS account, create an S3 bucket where Trivy-Operator’s reports will be stored.
- Set up permissions for access as needed.
Step 2: Export Reports to S3
Trivy-Operator doesn’t directly connect to S3, but you can use a Kubernetes job or custom script to export vulnerability reports to S3. Here’s an example:
kubectl get vulnerabilities -n <namespace> -o yaml > vulnerabilities_report.yaml aws s3 cp vulnerabilities_report.yaml s3://<your-bucket-name>/vulnerabilities_report/$(date +%F)_report.yaml
Step 3: Automate Backups
Set up a regular Kubernetes cron job to automate backups, ensuring that reports are consistently saved to S3 without needing manual intervention.
Conclusion
Trivy and Trivy-Operator work together to create a strong security solution for Kubernetes. From scanning container images during development to monitoring workloads in production, these tools offer full lifecycle security for your containerized applications. Connecting Trivy-Operator with Grafana and Prometheus helps your team stay alert to vulnerabilities, while backing up reports to S3 ensures you have a secure, long-term record for compliance needs.
By implementing these tools, you can protect your applications, respond effectively to security threats, and meet regulatory requirements with confidence.