In the ever-evolving landscape of cybersecurity, protecting your digital assets is paramount. In 2023, the average cost of a data breach is a staggering $5,000,000.
Don't wait until it's too late - take proactive measures to secure your Kubernetes deployment now. Here's your essential guide to Kubernetes security features that can safeguard your data and keep you one step ahead of potential threats.
-
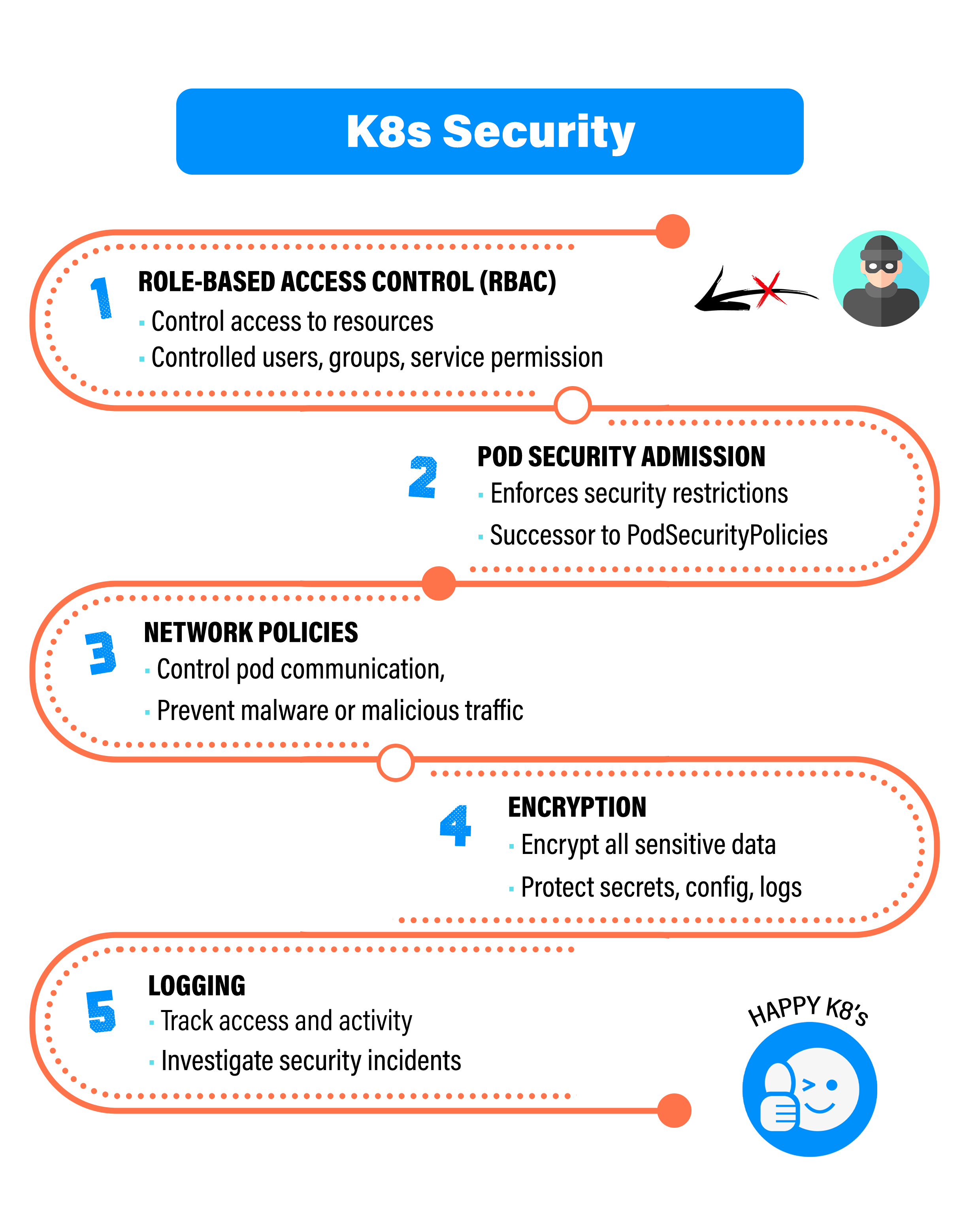
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is your first line of defense. It empowers you to control who has access to specific resources within your Kubernetes cluster.
By implementing RBAC, you can define fine-grained permissions for users, groups, and service accounts. This ensures that only authorized personnel can access critical components, minimizing the risk of unauthorized access or misuse.
-
PodSecurityAdmission (PSA)
With Kubernetes v1.25 and later versions, PodSecurityAdmission (PSA) has become the new standard, replacing the deprecated PodSecurityPolicy (PSP).
PSA adheres to Pod Security Standards (PSS), a comprehensive set of policies that outline essential security characteristics for workloads in your Kubernetes cluster. By embracing PSA, you enhance your cluster's security posture, making it resilient against potential vulnerabilities.
-
Network Policies
Network policies provide a robust framework for controlling pod-to-pod communication within your cluster and their interactions with the external world.
By defining explicit network policies, you prevent unauthorized access to pods, thwart the propagation of malware, and curtail malicious traffic. This proactive approach significantly mitigates the risk of security breaches originating from unregulated network traffic.
Encryption
Encryption serves as a safeguard for sensitive data at rest and in transit within your Kubernetes cluster.
By encrypting critical information such as secrets, configuration files, and application logs, you create an additional layer of security. This encryption ensures that even if unauthorized access occurs, the data remains incomprehensible and inaccessible, safeguarding your organization's confidentiality and integrity.
Logging and Audit Trails
Implementing audit logging is essential for maintaining a comprehensive record of activities within your Kubernetes cluster.
By tracking user interactions, you can swiftly identify suspicious behavior and investigate potential security incidents. Audit logs act as your digital trail, aiding in post-incident analysis and strengthening your overall security strategy.
Kubernetes is continually evolving, with new security features and bug fixes released regularly. Keeping your Kubernetes deployment up-to-date is crucial. Regular updates ensure that your cluster is fortified against the latest threats, vulnerabilities, and exploits. By staying current with the latest releases, you position your organization to proactively respond to emerging security challenges.
Conclusion
In conclusion, securing your Kubernetes deployment demands a proactive and multi-faceted approach. By implementing RBAC, embracing PodSecurityAdmission, defining stringent network policies, encrypting sensitive data, and maintaining comprehensive audit logs, you create a robust security framework. Remember, cybersecurity is an ongoing process. Stay vigilant, stay updated, and safeguard your digital assets effectively.