One of the first things you can do when beginning an e-commerce company is to think about and take steps to ensure the security of your platform. Neglecting this will result in serious consequences. Stolen business data may result in a lack of confidence from your customers, as well as more serious consequences such as compensation lawsuits.
What is WAF, and How does it work?
WAFs are based on a set of rules known as policies and can be deployed as hardware, software, or both in the cloud. These policies instruct the WAF firewall about what vulnerabilities/loopholes/traffic actions to check for, what to do if vulnerabilities are discovered, and so on. In other words, it is the policies that enable WAF to protect web applications and servers from attacks.
As a result of these rules, the web application firewall will continue to search web applications as well as GET and POST requests to detect and filter malicious activities and requests.
Web applications are protected by WAF against application-layer attacks and malicious HTTPS traffic.
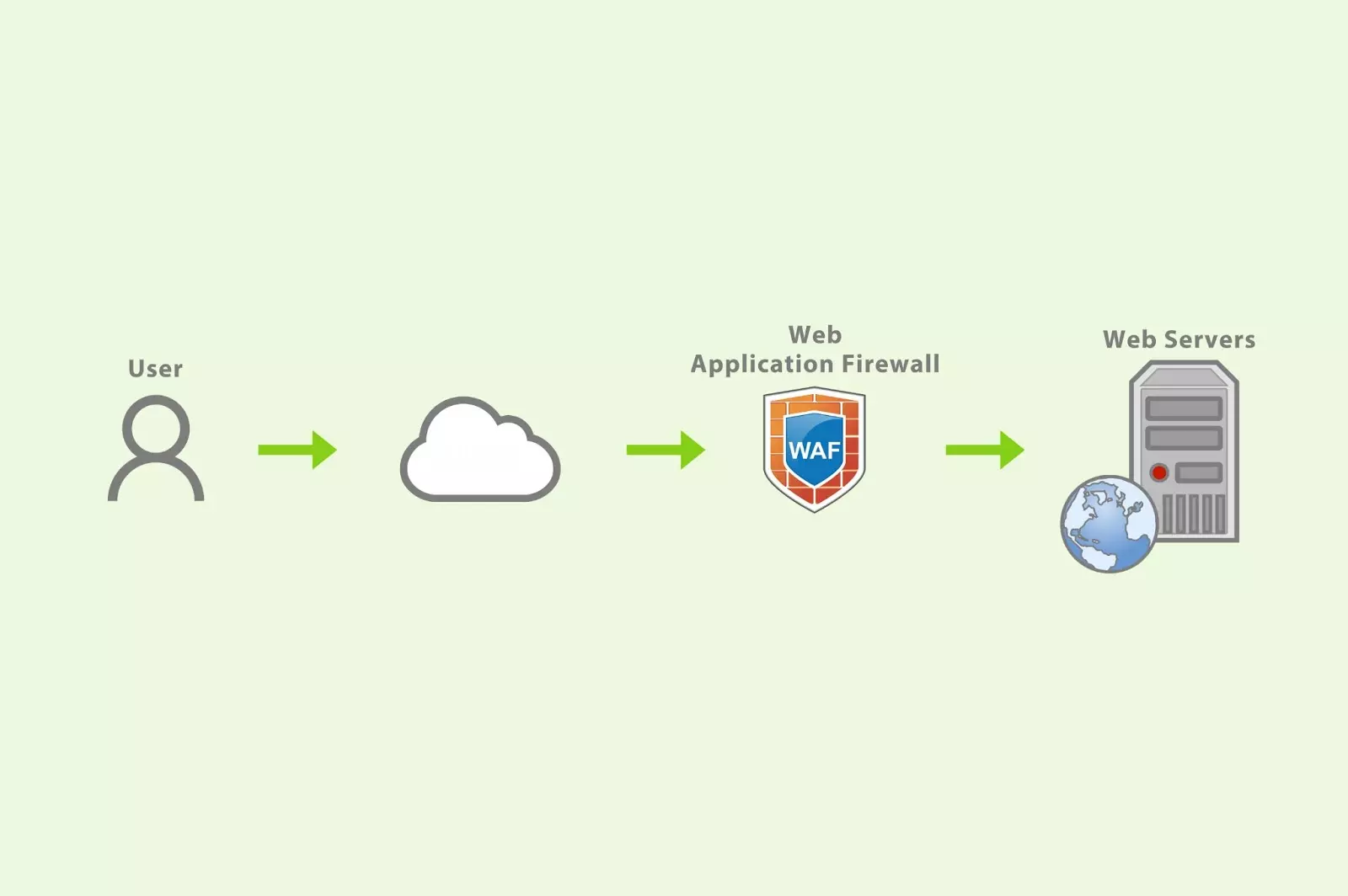
The various types of WAFs use slightly different procedures to deter malicious traffic. However, to boil it down to the simplest possible terms, it works like so:
- A user attempts to access your site either by clicking on a link or typing a URL into their browser. This sends an HTTP request to your server.
- Your WAF intercepts this request and analyzes it to determine if the user breaks any of your predetermined rules.
- if no rules are violated, the user’s request is passed on to your server, which returns the content they requested. In the event that their IP address is blacklisted or their activity is otherwise suspicious, your WAF will block them.
WAF's three main responsibilities are as follows:
- Monitoring
- Blocking
- Filtering
WAF attempts to prevent unauthorised data from leaving the app by enforcing a set of strict security policies that categorise which traffic is safe and malicious.
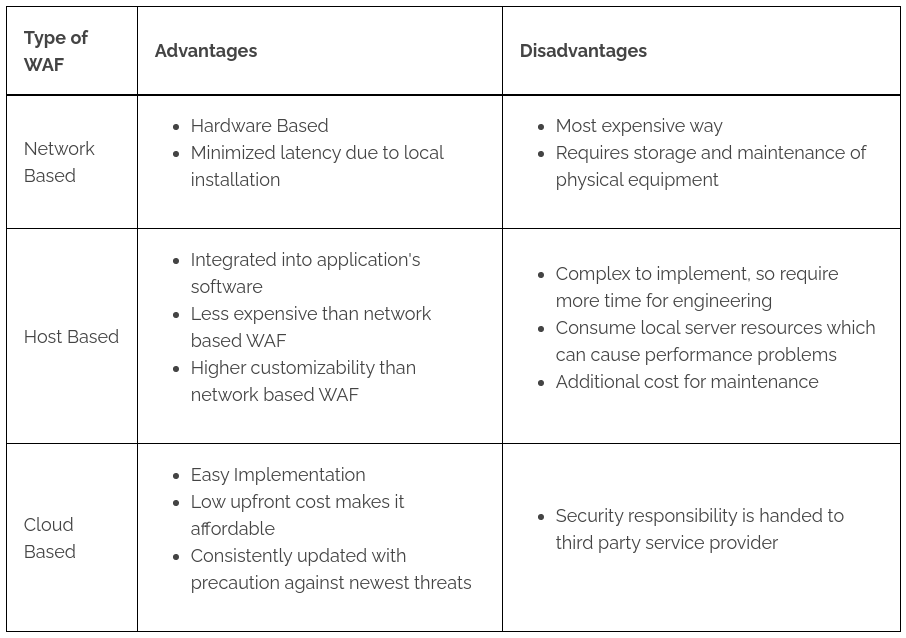
3 types of WAF :
WAFs operate on three levels, in addition to the types of rules they employ:
- Network Level : Network WAFs operate on a local level and typically require custom hardware solutions, making them prohibitively costly. They do, however, create less lag for users.
- Host level : This form of WAF is normally mounted on your server as a module or plugin. It's a lot less expensive than network-level solutions, but it uses some of your server's resources.
- Cloud Level : Software as a Service (SaaS) is a popular model for cloud WAFs. You usually pay a monthly fee in exchange for access to a solution that you can instal easily using your Domain Name System (DNS).
Each of them brings advantages and disadvantages :
AWS Web Application Firewall
Amazon Web Services offers a popular web application firewall solution (AWS WAF).
AWS WAF is a service that allows you to track and control HTTP and HTTPS requests forwarded to:
- An Amazon CloudFront distribution
- An Amazon API Gateway API
- An Application Load Balancer
You may describe the security strategy for a web access control list (ACL) that protects a collection of AWS resources by adding individual rules or reusable rule classes.The Amazon Web Services Web Application Firewall provides a variety of configuration options as well as a high level of security. Nonetheless, only the best would suffice for defence.
Conclusion
A Web Application Firewall is needed to meet your customers' security requirements when visiting your e-commerce site. Cloud-based WAF offers many advantages over network- or host-based WAF because of its ease of deployment and low costs. You can also run a routine Magento security scan to keep track of any potential security issues.Only an advanced solution is appropriate for you if you want to go beyond the standard WAF security.